- cross-posted to:
- [email protected]
- [email protected]
- cross-posted to:
- [email protected]
- [email protected]
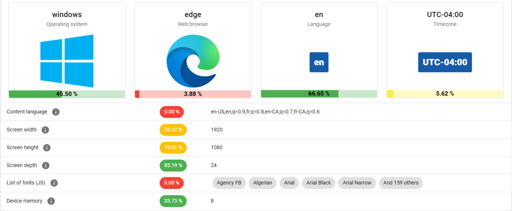
Amidst the glossy marketing for VPN services, it can be tempting to believe that the moment you flick on the VPN connection you can browse the internet with full privacy. Unfortunately this is quite far from the truth, as interacting with internet services like websites leaves a significant fingerprint. In a study by [RTINGS.com] this browser fingerprinting was investigated in detail, showing just how easy it is to uniquely identify a visitor across the 83 laptops used in the study.
As summarized in the related video (also embedded below), the start of the study involved the Am I Unique? website which provides you with an overview of your browser fingerprint. With over 4.5 million fingerprints in their database as of writing, even using Edge on Windows 10 marks you as unique, which is telling.


I’m here with multi-hop VPN with the first two hops staying in-country and the rest all random + a shit load of DNS blocking lists and browser extensions + blocking Google. I use different VPN providers too. I’m also introducing variable delays to my traffic to make NetFilter data less helpful.
Please understand that browser extensions make you more easy to track. I used to be under the same assumption, but uBO is as far as you should go. fingerprints include your extensions.
My thinking is that most of the fingerprinting is happening by third parties, and where it’s the website operators themselves I’m not super concerned about being fingerprinted.
Look at the uBO trackers on each site and you’ll br surprised how often Google comes up.
From their domain that I’ve already blocked with DNS? Or are you talking about first-party scripts calling Google (which I’ve also seen though much more rare)?
In any case I block those too.
Google tag manager, which would be first party scripts now.
That depends on whether your browser exposes them, and if/how they affect your fingerprint. If you go to deviceinfo.me it will show you what your browser is exposing.
Yeah, there’s also the covermytracks.eff.org and amiunique.org and https://abrahamjuliot.github.io/creepjs/index.html which is my favorite
deleted by creator
Some privacy browsers will randomize your fingerprint
deleted by creator
…no
I imagine it’s somewhere between what both of you are saying.
I imagine “randomized” means a random common “fingerprint” (with parameters like user agent, language, etc) rather than just a unique set of randomized parameters (say, time zone in US but language set to Farsi which would be unique to an extent).
I mean it doesn’t matter if it’s unique or not. What matters is that your fingerprint changes as you browse.
Sorry but that’s totally wrong.
The entire point is that if it’s unique it can be considered a fingerprint — in fact the entire reason it’s called “fingerprint” is that in theory it’s unique like a real fingerprint.
If it’s common then it’s unreliable as a fingerprint because it’s no longer unique. Therefore whether it’s unique or not is the entire point and relevant to the topic.
Sorry, but that’s totally wrong.
Imagine if you changed your literal fingerprint. No one would be able to trace it back to you.
Likewise, if your fingerprint changes as you browse, those activities can no longer be linked together, because you no longer have a “fingerprint” at all.
Right, that’s why I mentioned all the blocking at the DNS and browser extension level — most fingerprinting is being done by third-parties — I generally don’t see first parties fingerprinting but if they do it’s likely a website I chose to be on rather than some shady
<script>from God knows where.Laughs in Tails Linux